How to safely remove phishing from a WordPress site?
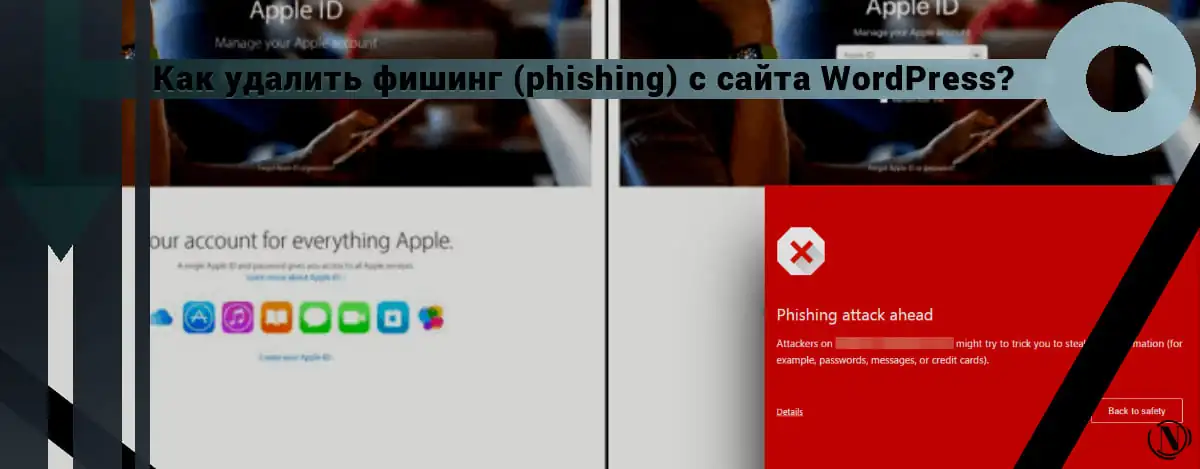
How to Remove Phishing from a WordPress Site? You are here because your visitors see a big red warning "this site is flagged as phishing" when they try to visit your site. But why do they see this warning? Your site is not phishing!
While there is a possibility that this is a false alarm, the first thing you should do is check your website for malware. If your website is clean, you can breathe a sigh of relief and skip to the section on how to appeal this warning. If not, keep calm, I will tell you exactly how to remove phishing from your site.
Most likely your site has been hacked and marked as dangerous by Google Safe Browsing. In particular, that this is a phishing site. You need to remove the malicious code immediately to get your site back to its original state.
The content of the article:
- What is a WordPress Phishing Hack?
- How dangerous is a WordPress phishing hack?
- How to know if there is a phishing scam on a WordPress website?
- How to Remove Phishing from Your WordPress Site
- How do I remove the "This site has been flagged as phishing" warning from Google?
- How to Prevent Phishing on a WordPress Site
- Types of Phishing Attacks
- How are phishing attacks detected?
What is a WordPress Phishing Hack?
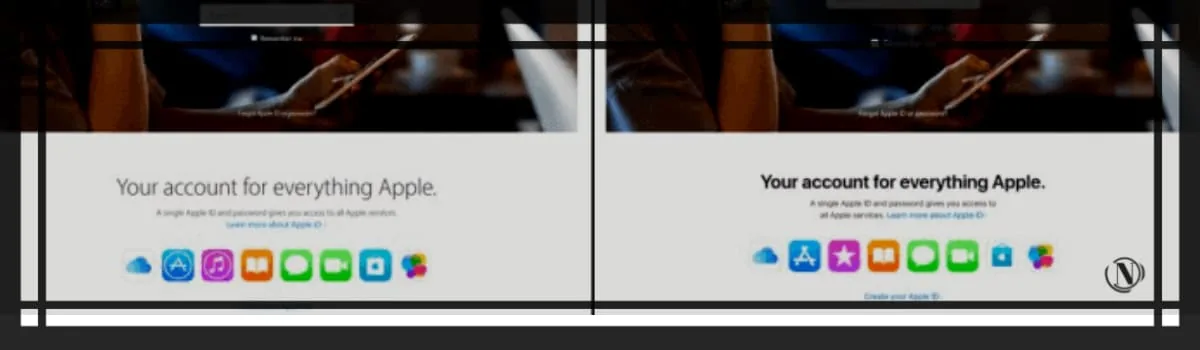
A WordPress phishing hack is when hackers trick unsuspecting users into revealing their identity and financial details by posing as a legitimate brand that the user trusts. This means that your website has official pages where people can share personal information.
How dangerous is a WordPress phishing hack?
Phishing attacks cost businesses billions of dollars every year. In the first 6 months of 2020 alone, 313,778 phishing sites were discovered. A phishing attack is very dangerous for any website.
All malware is destructive and must be dealt with first. You've already spent some time figuring out what went wrong, but remember that every minute that malware stays on your site, you're incurring a loss.
How to get rid of phishing should be a top priority. Later in this article, I will tell you how to remove phishing by yourself.
But to be clear, removing malware manually is not an easy task, and I do not recommend doing it under any circumstances. A hacked website can have multiple infestations, backdoors and hidden fake admins due to malicious files like favicon_bdfk34.ico and many more. Trying to find and remove them all on your own is a surefire way to completely ruin your site.
I strongly recommend that you use a security plugin that will instantly remove phishing from your website without any delay.
How to know if there is a phishing scam on a WordPress website?
If you haven't experienced phishing campaigns yourself and have seen Google warnings that this site is flagged as a phishing site, you might be wondering if your site has indeed been hacked. There is a sure way to exclude the possibility of hacking:
- Check Google Search Console > Security Questions for false content.
- Visit some of the tagged URLs in the report from a different computer, network, or incognito mode. Hackers can mask malware from website administrators to prolong infection.
- Check for third party inclusions on your website. Ad networks may sometimes serve ads with phishing campaigns. Because ads tend to cycle, you may need to refresh your website several times to check the ads you see. Even if the ad uses social engineering, your website may still be flagged as containing misleading information.
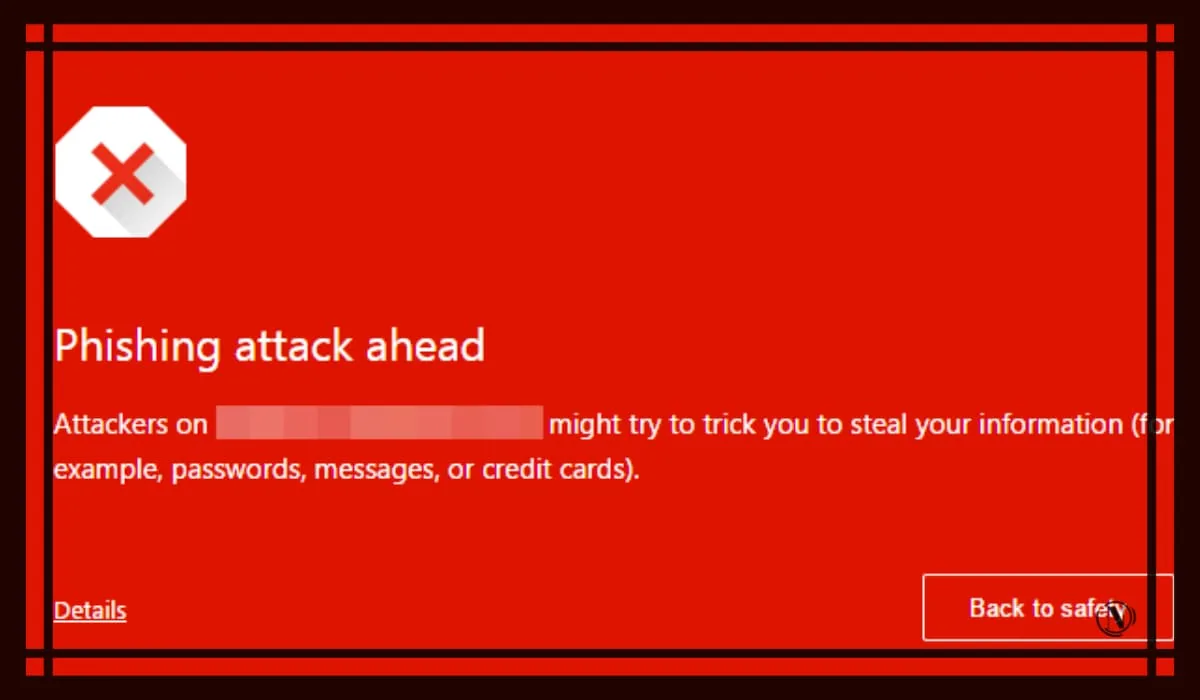
If Google Search Console flags issues, you can be sure that your website has been the victim of a WordPress phishing hack and you can proceed to remove the phishing.
How to Remove Phishing from Your WordPress Site
There are several ways to remove phishing pages from your WordPress site as soon as possible.
The fastest way to get rid of phishing is to use a security plugin to safely remove it without compromising your website. After that, you can appeal the warning.
Alternatively, you can remove WordPress phishing manually. To be clear, this process involves digging through code to find pages and therefore malware. Phishing pages will not be easily visible in your database, they will be hidden in various system files and directories in your content management system.
Only experienced developers should remove phishing files, as there is a chance that you will remove the necessary code and cause irreparable damage to the site. Be careful when deleting the following pages:
- Pages you didn't createA: Some phishing pages will mimic your website's design, content, and branding as closely as possible to look legitimate and remain undetected for as long as possible.
Phishing pages will basically be login and payment pages: – because that is the type of information that hackers aim to capture. - Bank or e-commerce branded pages: Since phishers impersonate a legitimate person, they copy their brand to do this. You will likely find logo files, perhaps in a favicon file, and a few image files that are used to reproduce the official branding.
- Unfamiliar folders: that appear to belong to another object.
- Wrong checkout pages: on your own e-commerce pages, if you have them. Hackers can redirect your own customers from your pages.
As an added insurance, make a fresh backup of your website before removing phishing. If something goes wrong, you'll still have the infected website you started with, and you can opt for one-click cleanup instead.
How do I remove the "This site has been flagged as phishing" warning from Google?
The review process takes an average of 72 hours. It is extremely important to be sure on the 100% that the phishing removal was successful. Otherwise, your request will be rejected and the process will take even longer.
Here are the steps to remove the warning "this site has been flagged as a phishing site»:
- Return to Google Search Console > Security Issues.
- Check the box - I fixed these issues And Request a review.
- You will need to provide details of what steps you have taken to remove the phishing.
Why is WordPress vulnerable to phishing?
By its very nature, WordPress should be easy to use as well as easily customizable through themes and plugins. These additional pieces of software are designed to add features and functionality, but do not always provide the best practices for keeping your site secure. Therefore, they force the site to have weak (vulnerabilities) entry points.
You can't completely abandon themes and plugins, and it's not really a solution. The best way is to take preventive measures and eliminate vulnerabilities.
How to Prevent Phishing on a WordPress Site
Malware infiltrates WordPress due to vulnerabilities. Hackers exploit vulnerabilities to gain access and inject their malicious code snippets into a website. Quite often, website administrators are not even aware of these events until something goes wrong. And by that time, significant damage and losses had already taken place.
1. Install the security plugin
I can't stress enough the importance of installing a good security plugin. You don't want to be caught off guard after a visitor, your web host, or Google has informed you of a problem with your site.
Choose a plugin that is primarily able to prevent the installation of malware and includes a strong firewall. If malware is found on your website, the plugin should be able to remove it without putting your website at risk and ensuring that the content remains intact. And finally, choose a plugin that has an expert manual removal service.
2. Remove backdoors on the site
This important step in prevention is difficult to do well because backdoors can be hidden in the main folders (the default folders). What makes removal even more difficult is that many features are used by plugins for benign reasons. Thus, removing a feature that might appear to be a backdoor can lead to unforeseen consequences. I don't recommend doing it yourself.
3. Remove unauthorized users
Check your database to identify and remove unverified users. Be careful not to delete real users. Also change all administrator passwords after phishing is removed.
4. Update your site
A simple but often overlooked security method is to keep your WordPress and all installed plugins and themes up to date. Updates include security fixes that address vulnerabilities, among other things, and must be installed on a priority basis. If there are plugins or themes that you don't actively use, disable or remove them.
5. Install an SSL certificate
Most web hosts include SSL certificates with their services. SSL certificates encrypt data that is transmitted between browsers and servers. It's very easy to set up and use, and is actually a Google requirement for safe browsing, as well as removing the site's insecure warning on your site's padlock.
6. Require strong login credentials
Easy-to-guess usernames and passwords are still one of the easiest ways for a hacker to gain unauthorized access to a website. All users should be required to set strong passwords for their accounts.
Types of Phishing Attacks
Phishing itself is a type of social engineering attack, which essentially means that the attack is based on pretending to be someone else in order to succeed. In addition, social engineering attacks rely on the victim willingly providing their information because they believe the request is legitimate.
Phishing WordPress Hack
A hacker inserted official pages into your live website to trick people into pretending to be a brand. While this is bad enough, consider that you may have been the victim of a phishing attack because…
Targeting Website Administrators
Sometimes you are harassed because of your administrator credentials so that hackers can gain access to the websites you control.
You may have received an email asking you to "urgently" update your database or something terrible will happen. The email will take you to a page that looks like your web host or admin panel to update the database by entering your credentials.
Or perhaps the scammer is posing as an angry customer and demanding a refund. Look out for glaring grammatical errors, and while the email mentions an attachment, it contains a link.
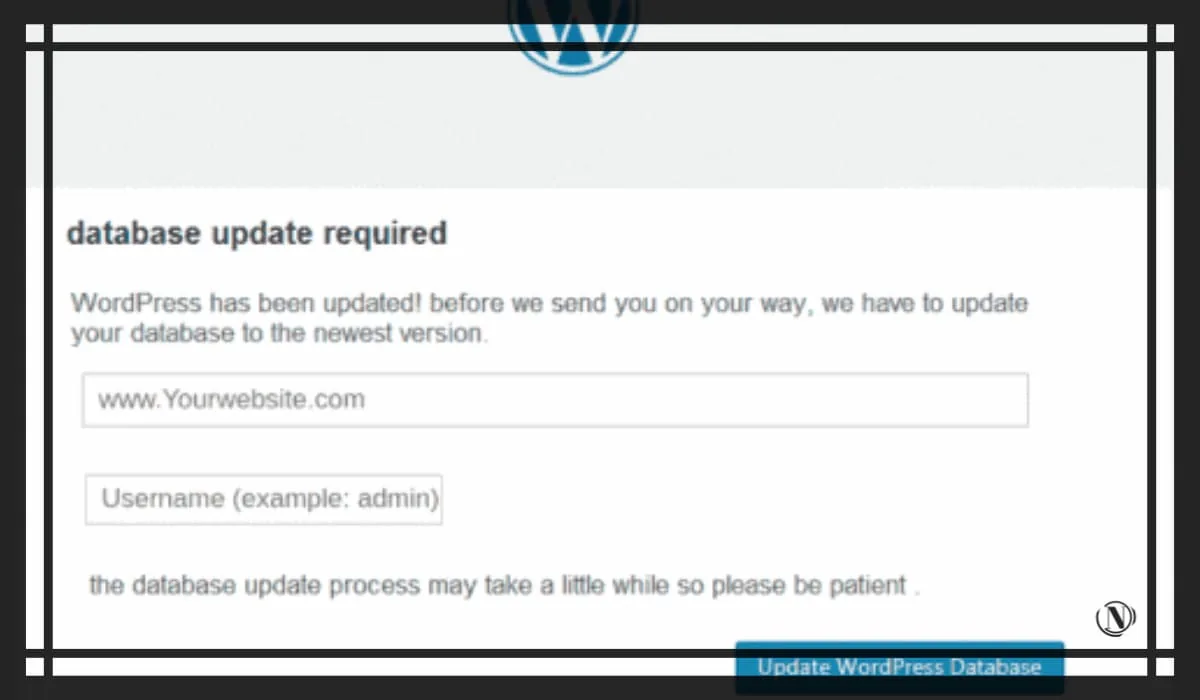
Even WordPress professionals with years of experience can sometimes be scammed by these emails, especially if they manage multiple websites and handle all those websites' operations in different locations.
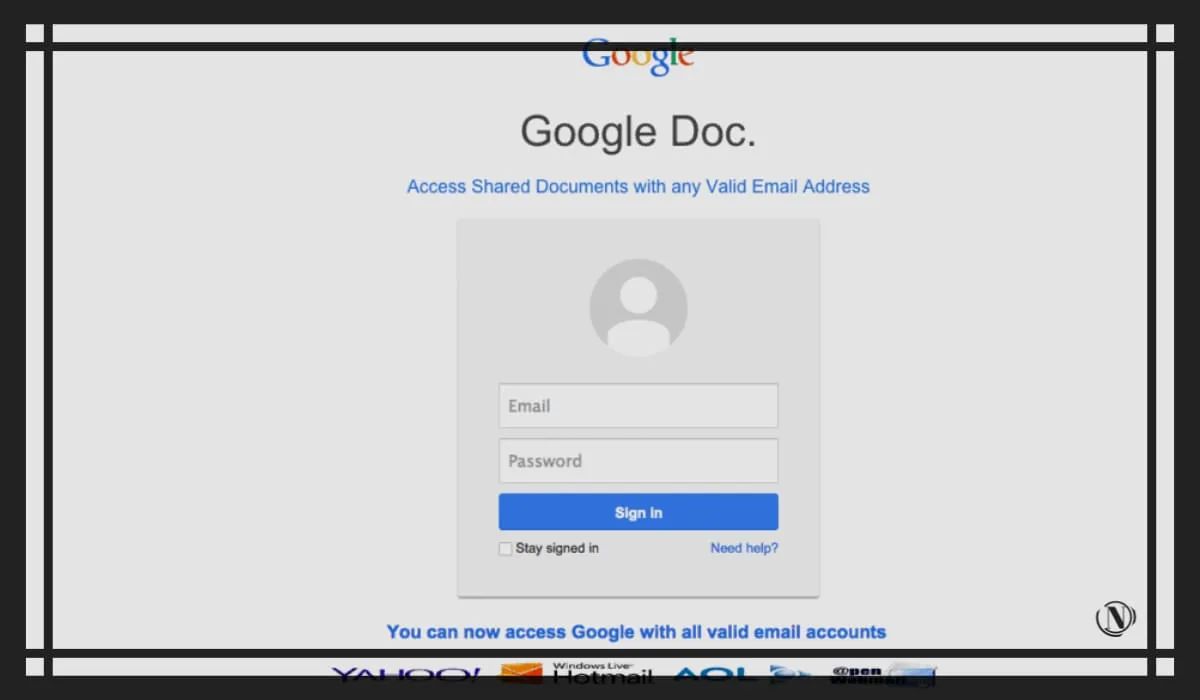
Email Phishing vs WordPress Phishing Hack
There are different types of phishing: using email, hosting malicious web pages, and most often a combination of the two. Hackers insert pages into your website that appear to be from a trusted organization in order to obtain their login credentials. Typically, an unsuspecting user will land on this scam page via email, but they can also stumble upon it via a link or a redirect.
fun fact: There is a special category of phishing attacks that use the Google brand. Yes, the mighty Google has not escaped this threat either. In fact, they have a dedicated support page for misleading pages perpetuated in their name.
Individual and spear phishing
Phishing attacks target large groups, so one of the clear signs of a phishing email is a lack of personalization. This isn't to say that all automated emails are suspicious, but if an email asks for sensitive data such as bank card details or login credentials, the lack of personalization can be a red flag.
Except when it comes to spear phishing attacks. These types of attacks target specific individuals in order to transfer their data.
Collecting login credentials may not be a big problem for individual websites, but it becomes a way to connect to the secure environment of that website (and its organization) if, for example, the credentials belong to an employee.
In addition, we tend to use the same credentials on different websites and devices, and these accounts may contain sensitive information.
How are phishing attacks detected?
The most unfortunate way to know that your website has a WordPress phishing hack is to get blacklisted by Google and your visitors will see one of the warning messages like this site is flagged as phishing if you don't have a reliable security plugin installed.
Phishing websites are currently being detected using sophisticated artificial intelligence. However, they are also reported by people on Google who come across them.
As we increasingly use devices and the internet to complete tasks in our daily lives, internet security is now something of a parable. Everyone gets tips and tricks to keep their data safe from every brand they interact with, from the government to their bank to their grocery delivery app.
These posts contain practical ways to detect a phishing attack from a mile away: check the sender (for emails), check the URL (for websites), whether there is unnecessary pressure on someone to perform a certain action, etc.
Phishing attacks are also becoming more sophisticated, increasingly mimicking the language and branding of trusted organizations. Therefore, in order to protect its users from being scammed, Google is especially vigilant about hacked websites.
Conclusion
Hope the phishing removal was successful and your website is up and running again and free of malware. I hope the information in this article has been helpful to you.
Reading this article:
- How to remove WP-VCD.php malware from your WordPress site
- How to remove Favicon.ico virus from your WordPress site?
Thanks for reading: SEO HELPER | NICOLA.TOP








Removed using the module, according to this article. Thanks for the info!
Thanks for the feedback Natalie) I'm glad that the guide was useful to you.